3 Tier Technologies
Adding tiered, secured, innovative and natural solutions that are right for the times.
Contact us
Adding tiered, secured, innovative and natural solutions that are right for the times.
Contact usAccording to the Software Engineering Institute, about 90% of reported security incidents result from exploits against defects in the design or software code. With vast experience in Application Security, Architecture and Automation, we at 3TT are focused to address today’s Security by Design challenges in a unique way by adapting a Platform centric approach and Automated Threat Modelling.
Our experts have worked in Automotive, Telecom, Healthcare, Federal/State Agencies, and Financial industries. Contact us for your Architecture and Cyber Security needs and we will work with you to scope scalable solutions specific to your organization.

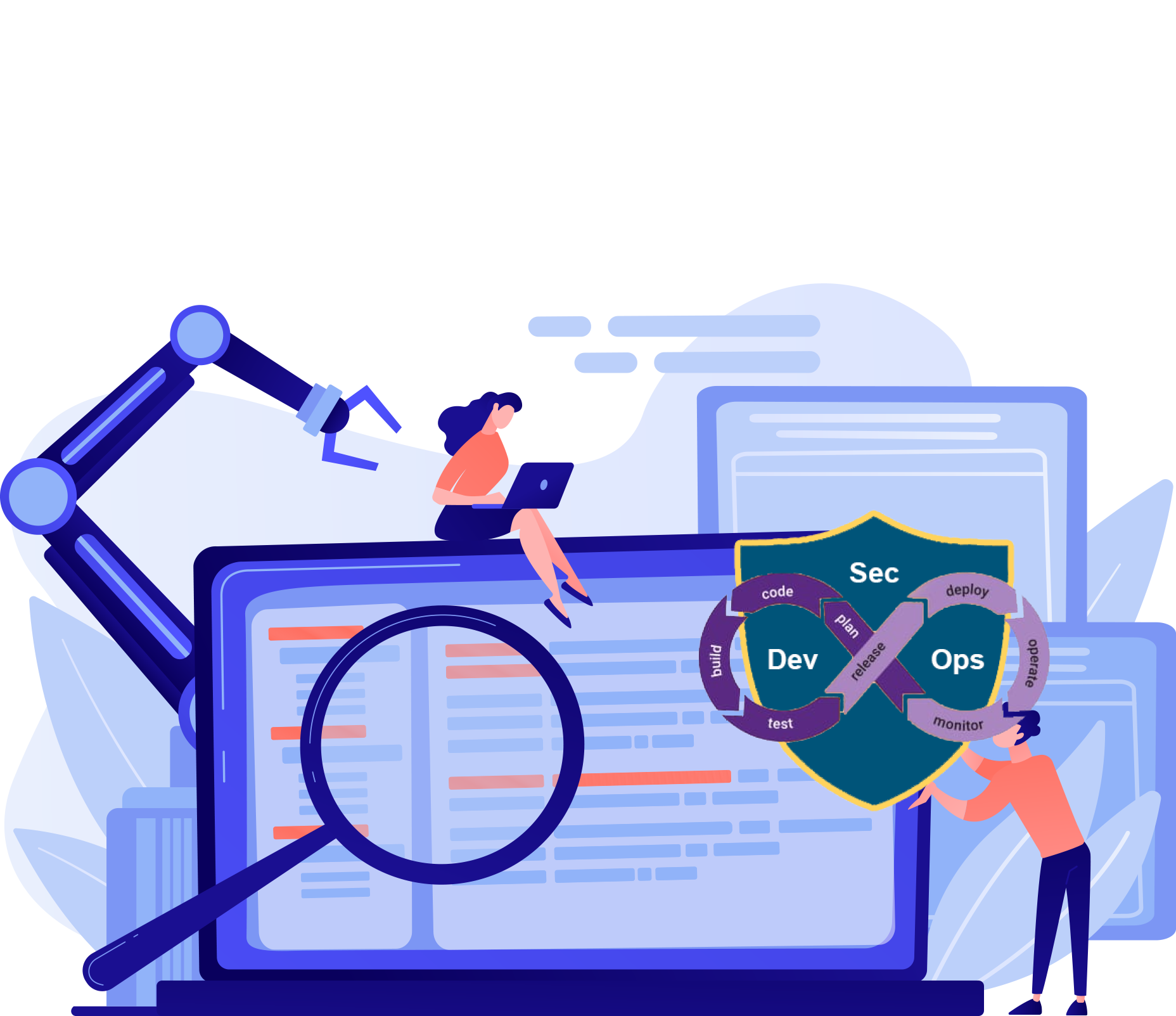
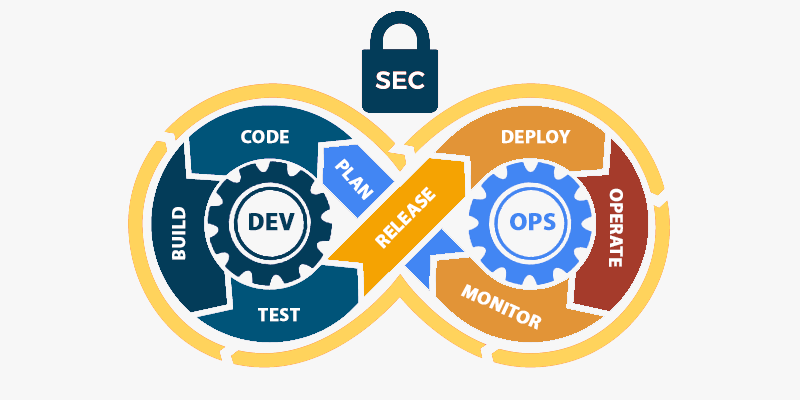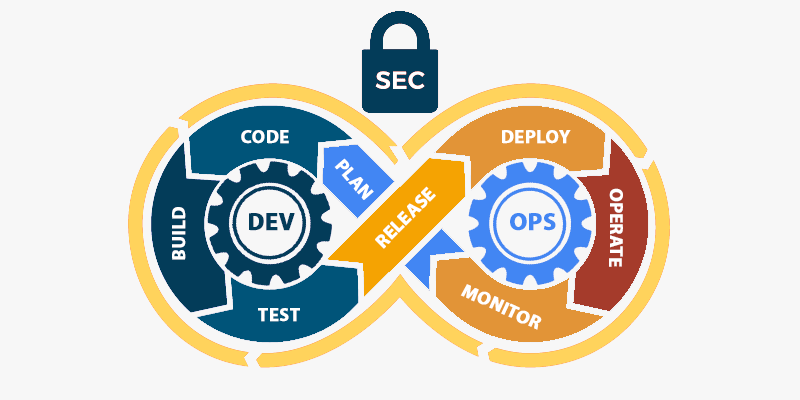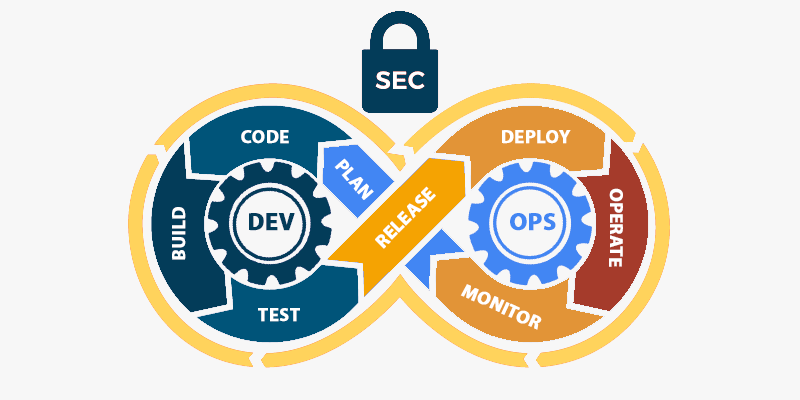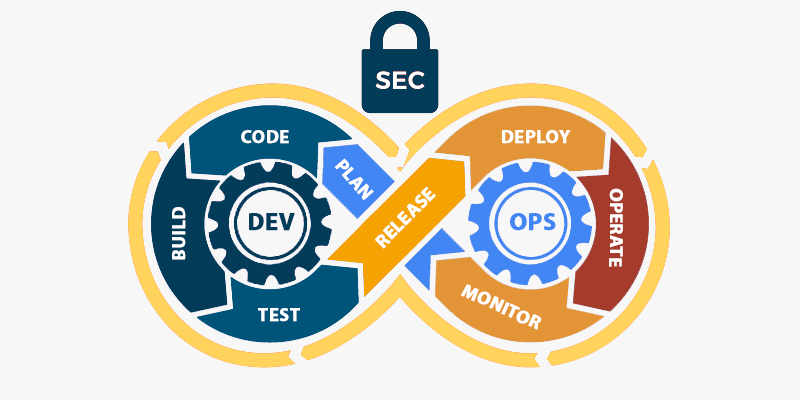
Moving from DevOps to DevSecOps is not a simple proposition, but can be achieved successfully in phases. 3TT’s automated authorization policy enforcement solution can help manage security across the entire tech stack, and enable uniform security design principles at each phase.
3TT ran by experts, drives our customers towards a pattern-oriented architecture and templatize those patterns to make them portable for automation.
3TT provides organizations an expert analysis without the cost of a full-time consultants. We have a track record of providing solution automation and assemble it seamlessly to deliver prompt and lasting business benefits
"Security Package for DevSecOps" is a collection of standards, directives, security patterns and controls that caters to end to end security automation for DevOps
Security Package provides ready access to the information required for operational requirements. It contains product-neutral information allowing integrators to implement their own solutions
Security Package provides sufficient guidance for accreditors to make informed decisions on solutions to meet the security requirements
Security Package delivers declarative authorization policy-as-code for cloud-native solutions using general-purpose policy engine
We help drive detailed architectural support by, translating Enterprise & Technical strategies into deliverable and cost-effective solution artifacts. This includes SAFe™ Architecture Enablers, Spikes, User Stories/Epics and Solution Design. 3TT architects will work hand in hand with technical experts, users and strategic leadership using AAA layers
Gap and Overlap Analysis centered on agreed metrics. Production of “Reference”, “As Is”, “To Be” (Target) Architecture and Cloud Security.
Industry best practices assured through TOGAF governance, Standards and Patterns. Architecture Languages: ArchiMate, BPMN, SysML and UML.Tools: BIZZDesign, Visio and Sparx EA.
Establish automation roadmap for tools and process. Determine retention and business continuity policies for automated workflows. Create Service Design Packs utilizing Solution Building Blocks and Infrastructure as Code
Ideal time to perform threat modeling is in the earliest stages of the SDLC. 3TT will examines the design of system operations and how data flows across subsystem boundaries, and implement simple threat modeling practices at the backlog
3TT consultants are the experts in NIST CSF, ISO27001, GDPR compliance projects. We have been assisting our customers comply with State and Federal regulations. 3TT will work either a full-service consultant, or as an adjunct to your in-house teams for phased compliance readiness process to meet or exceeds compliance requirements
We provide technical and strategic support to businesses across the automotive industry, giving our team unrivaled collective experience and a unique perspective. Specializing in partner selection, program management, technology design & development
3TT provides the ability to modernize legacy applications using SecuredCloudOps, or, the operation of the application containers and microservices in the cloud.
3TT multiplies the effectiveness of your solutions by providing expert level guidance. The more 3TT integrates with your team the better understanding of the environment and faster turnaround on guidance.
Contact us










